CrossFit is all about chaining assaults mutually to get the goal to do my bidding. It starts offevolved with a cross-site scripting assault in opposition to a website. The website detects the attack, and forwards my consumer agent to the admins to investigation.
An XSS payload within the user-agent will trigger, giving some entry there. I'll dig a hash out of ansible configs and crack it to get the subsequent user. To escalate again, I'll exploit a command injection vulnerability in a PHP plugin, php-shellcommand, by writing to the database. To get root, I'll reverse engineer a binary that runs on a cron and work out learn how to trick it to put in writing a SSH key into root's authorized_keys file. I'll attain entry to an occasion of Supervisor Process Manager, and use that to leak a course of list, which exhibits the place to look on the port eighty webserver. I'll discover an API that I know is backed by a Lua script, and exploit a command injection vulnerability to get execution and a shell.
I'll get credentials for a webserver listening on localhost and discover an SSH key hosted there to get to the second user. That consumer can doas arbitrary instructions as root, the password is needed. It's in an encrypted backup file which might be decrypted utilizing PGP on the host. In Beyond Root, I'll take a look on the Lua script, work out the way it works, the place the injection vulnerability is, and examine that to the patched dev adaptation to see the way it was fixed. At the time of writing three days earlier than it retires, simply over one hundred folks have rooted it, making it the least rooted field on HackTheBox. It begins with a phishing training the place hints betray that the consumer will open a textual content file in Vim, opening them to the Vim modelines exploit to get command execution.
But there's a firewall blocking any outbound visitors that isn't ICMP or a legitimate HTTP GET request, so I'll write some scripts to construct command and management via that. Then I discover a spot I can drop an SSH config file that may be run by the second user, which I'll abuse to get SSH access. For root, there's a buffer overflow in a command processing SSH auth on the gateway.
I'll craft a malicious SSH key to overflow that binary and get a reverse shell. In Beyond Root, I'll check out an unintended command injection within the SSH config operating script. Kotarak was an previous field that I had a very enjoyable time replaying for a writeup. It begins with an SSRF that permits me to search out further webservers on ports solely listening on localhost.
I'll use that to leak a Tomcat config with username and password, and addContent a malicious struggle to get a shell. From there, I can entry documents from an previous Windows pentest to incorporate an ntds.dit file and a system hive. That's sufficient to dump a bunch of hashes, certainly one of which cracks and delivers creds I can use to get the subsequent user.
The root flag is definitely in a container that's making use of Wget to request a file each two minutes. It's an previous weak version, and a very neat exploit that includes sending a redirect to an FTP server and making use of that to put in writing a malicious config file within the basis house listing within the container. I'll additionally present an alternate root abusing the user's disk group to exfil the whole root filesystem and seize the flag on my native system. With social engineering, moral hackers exploit human psychology, other than technical safety gaps to realize entry to facts and applications. They trick official customers into submitting their passwords or putting in malicious software program that grants them entry to community machines and services.
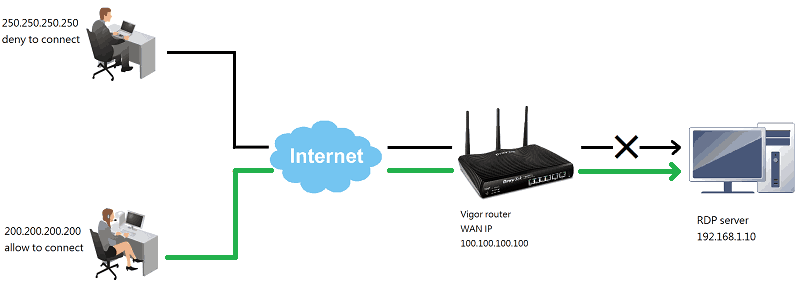
It is primary expertise that human customers are the weakest hyperlink for cyber security, so moral hackers perform social engineering simulations to evaluate organization-wide understanding of safety controls. The open port that resides on the worldwide public IP tackle the place the VPN is hosted is the basis explanation for the present safety dilemma. A VPN server by definition need to reside at a routable world IP tackle and supply an open port the place respectable customers can provoke a connection and log in with their username and password.
The obstacle is that open ports are additionally susceptible to unsolicited inbound traffic. It introduced a component of math / crypt into a lot of the challenges in a method that I genuinely enjoyed. But it nonetheless layered challenges in order that every step concerned a number of exploits / bypasses, like all good insane packing containers do. I'll start off by gaining entry to a online net net net net net page by telling the net net net net net page to validate logins in opposition to a database on my box. The net website offers me that capacity to return encrypted webpage content material that Kryptos can retrieve. I'll break the encryption to entry pages I'm unable to entry on my own, discovering a sqlite check net net net net net page that I can inject into to write down a webshell which can entry the file system.
With file system access, I'll retrieve a Vim-crypted password backup, and crack that to get ssh entry to the system. On the system, I'll entry an API obtainable solely on localhost and make the most of a weak random wide variety generator to signal my very personal commands, bypassing python protections to get code execution as root. I'll use snmp to get equally the IPv6 tackle of the host and credentials from the webserver. From there, I can use these creds to log in and get extra creds. That website has command injection, which provides me code execution, a shell as , and creds for loki. Loki's bash records provides me the basis password, which I can use to get root, as soon as I get across the truth that file entry manipulate lists are used to stop loki from operating su.
In previous root, I'll inspect how I may get RCE with out the creds to the website, how I may need exfiled files by means of ping if there wasn't a option to see output, the filtering that website did, and the iptables rules. Cereal was all about takign assaults I've executed before, and breaking the techniques I've beforehand executed them in order that I needed to dig deeper and virtually fully grasp them. The website is inbuilt C#/.NET on the backend, and React JavaScript on the consumer side. I'll first should discover the code that generates authentication tokens and use that to forge a token that will get me previous the login. There I even have entry to a kind which will submit cereal taste requests.
I'll chain mutually a cross-site scripting vulnerability and a deserialization vulnerability to addContent a webshell. That was made extra tough since the serverside code had logic in place to interrupt payloads generated by YSoSerial. With execution, I'll discover the primary consumer password and get SSH access. But with no print spooler service on the box, and no outbound TCP port 135, neither RoguePotato, SweetPotato, or PrintSpoofer might abuse it to get a SYSTEM shell. I'll enumerate a website operating on localhost and its GraphQL backend to search out a serverside request forgery vulnerability, which I'll abuse with GenericPotato to get a shell as System.
Fluster starts offevolved out with a coming quickly webpage and a squid proxy. When equally finish up as lifeless ends, I'll establish GlusterFS, with a quantity I can mount with no auth. This quantity has the MySQL facts stores, and from it I'll discover Squid credentials. With entry to the proxy, I'll discover the appliance supply code, and exploit a server-side template injection vulnerability to get execution. With a foothold, I'll discover the keys essential to get entry to a second Gluster volume, which provides entry as user. To root, I'll hook up with a Docker container internet hosting an emulated Azure Storage, and making use of a key from the host, pull the basis SSH key.
In Beyond root, an exploration into Squid and NGINX configs, and a inspect full recreating the database established on the statistics from the distant volume. Ethical hackers additionally depend on social engineering strategies to control finish customers and acquire details about an organization's computing environment. However, there are social engineering strategies that moral hackers shouldn't use, resembling making bodily threats to staff or different different varieties of makes an try to extort entry or information. Smasher is a very onerous field with three challenges that require an in depth understanding of how the code you're intereacting with works. It starts offevolved with an occasion of shenfeng tiny-web-server operating on port 1111. I'll use a path traversal vulnerability to entry to the basis file system.
I'll use that to get a replica of the supply and binary for the operating net server. With that, I'll write a buffer overflow exploit to get a reverse shell. Next, I'll exploit a padding oracle vulnerability to get a replica of the smasher user's password. From there, I'll reap the benefits of a timing vulnerability in setuid binary to learn the contents of root.txt. I assume it's available to get a root shell exploiting a buffer overflow, however I wasn't ready to tug it off .
In Beyond Root, I'll take a look at the AES script, and present how I patched the checker binary. FluJab was an extended and not easy box, with a number of sophisticated steps which require a number of items working mutually and cautious enumeration. I'll commence by enumerating a number that hosts net websites for a lot of various customers, and is supposed to be like a CloudFlare ip. Once figuring out the host I'm targeting, I'll discover some bizarre cookie values that I can manipulate to get entry to configuration pages.
There I can configure the SMTP to undergo my host, and use an SQL injection in a single of many varieties the place I can learn the outcomes over email. Information within the database credentials and new subdomain, the place I can entry an occasion of Ajenti server admin panel. That permits me to establish weak ssh keys, and to add my host to an ssh TCP Wrapper whitelist.
From there, I'll discover a weak model of display which I can use to get a root shell. In Beyond Root, I'll present an unintended path to get a shell applying Ajenti applying the API, examine the small print of the display exploit, discover the box's fresh up crons, and indicate an oddity with nurse jackie. Patents was a very powerful box, that very likely must have been rated insane. I'll discover two listening services, a webserver and a customized service. I'll exploit XXE in Libre Office that's getting used to transform docx information to PDFs to leak a configuration file, which uncovers yet another part of the site.
In that section, there's a listing traversal vulnerability that permits me to make use of log poisoning to get execution and a shell within the net docker container. To get root in that container, I'll discover a password within the method list. As root, I get entry to an software that's speaking with the customized service on the host machine. I'll additionally discover a Git repo with the server binary, which I can reverse and discover an exploit in, leading to a shell as root on the host machine.
In Beyond Root, I'll study chaining PHP filters to exfil bigger information over XXE. The majority of the field was reversing and modifying a Java thick client. First I needed to switch the consumer to get the consumer to connect. Then I'll make the most of a listing traversal vulnerability to get a replica of the server binary, which I can reverse as well.
In that binary, first I'll discover a SQL injection that permits me to log in as an admin user, which offers you me entry to further functionality. One of the brand new capabilities makes use of serialized objects, which I can exploit making use of a deserialization assault to get a shell within the container operating the server. Escalation to root assaults a recurring course of that's making use of SCP to repeat an archive of log data off the container to the host. Travel was simply an exceptional field since it furnished a posh and difficult puzzle with new items that have been enjoyable to explore. I'll start off out digging via varied vhosts till I sooner or later discover an uncovered .git folder on one. That offers you me the supply for another, which incorporates a customized RSS feed that's cached making use of memcache.
I'll consider that code to search out a deserialization vulnerability on the learn from memcache. I'll discover a hash within the database which I can crack to get a password for the consumer on the principle host. This consumer can additionally be the LDAP administrator, and SSH is configured to ascertain LDAP for logins. I'll choose an arbitrary consumer and add an SSH exclusive key, password, and the sudo group to their LDAP such that then once I log in as that user, I can simply sudo to root. In Beyond Root I'll discover a bizarre conduct I noticed within the RSS feed. Compromised includes a field that's already been hacked, and so the problem is to comply with the hacker and each exploit public vulnerabilities in addition to make use of backdoors left behind by the hacker.
I'll discover an internet website backup file that reveals how the login net page was backdoored to file admin credentials to an internet accessible file. With these creds, I'll exploit a weak LiteCart instance, even though the general public exploit doesn't work. I'll troubleshot that to seek out that the PHP capabilities traditionally used for execution are disabled. I'll present two methods to work spherical that to get entry to the database and execution because the mysql user, who's shell has been enabled by the hacker. As the mysql user, I'll discover a strace log, doubtless a makeshift keylogger utilized by the hacker with creds to pivot to the subsequent user.
To get root, I'll reap the benefits of both of two backdoors left on the field by the attacker, a PAM backdoor and a LDPRELOAD backdoor. In Beyond Root, I'll present tips on how to run instructions as root employing the PAM backdoor from the webshell as To start, I can connect, however there's on the very least one username I can't access. I'll discover a pet-themed website on a digital host, and discover it has an uncovered git repository. Looking on the code reveals file learn / listing traversal and command injection vulnerabilities. From localhost, I can entry the chat for the primary user, the place there's background displaying an additional consumer telling them about an influxdb instance.
I'll discover an auth bypass exploit to examine the db, and get the subsequent user's password. This consumer has entry to the supply for a brand new edition of Devzat. Analysis of this edition exhibits a brand new command, comprehensive with a file examine vulnerability that I'll use to examine root's exclusive key and get a shell over SSH. Ethical hackers assist corporations decide which of their IT safety measures are effective, which want updating and which include vulnerabilities that may be exploited.
Organizations can use the information from these checks to make knowledgeable choices about the place and the way to enhance their safety posture to forestall cyber attacks. At the start, it required enumerating an internet net site and discovering a png file that was truly a textual content file that exposed most of a password. I'll use hydra to brute drive the final character of the password, and achieve entry to a Moodle instance, program designed for on-line learning. I'll abuse a PHP injection within the quiz function to get code execution and a shell on the box.
Then, I'll discover an md5 within the database that's the password for the primary consumer on the box. From there, I'll profit from a root cron that's operating a backup script, and provides myself write entry to anything I want, which I'll use to get root. If you'd like knowledge to to come again that up, the primary blood occasions of over 1.5 and 2.5 days!
I keep in mind vividly engaged on this field with all my free time, and being the fifth to root it within the sixth day. I'll start off by discovering a hosts whose major assault level is a GoPhish interface. This interface offers up some domains for faux phishing websites on the identical host, which I can use to seek out an admin interface which I can abuse to get file system entry by way of log poisoning.
Unfortunately, all of the features I should get RCE by way of PHP or ASPX are disabled. I can nonetheless addContent reGeorge and use it to tunnel a connection to WinRM, the place I can use some creds I discover in a config file. From there I can abuse a defective service that permits me to put in writing as SYSTEM wherever I wish to overwrite a file in SYSTEM32, after which use DiagHub to get a SYSTEM shell.
The first half of Oouch constructed throughout OAuth, a technologies that's commonplace on the web today, and but I didn't comprehend properly coming into the challenge. This field pressured me to realize an understanding, and scripting this submit cemented that even further. To get user, I'll exploit an insecure implementation of OAuth by way of a CSRF twice.